0 Comments
0 Shares
6 Views

Directory
Elevate your Sngine platform to new levels with plugins from YubNub Digital Media!
-
Please log in to like, share and comment!
-
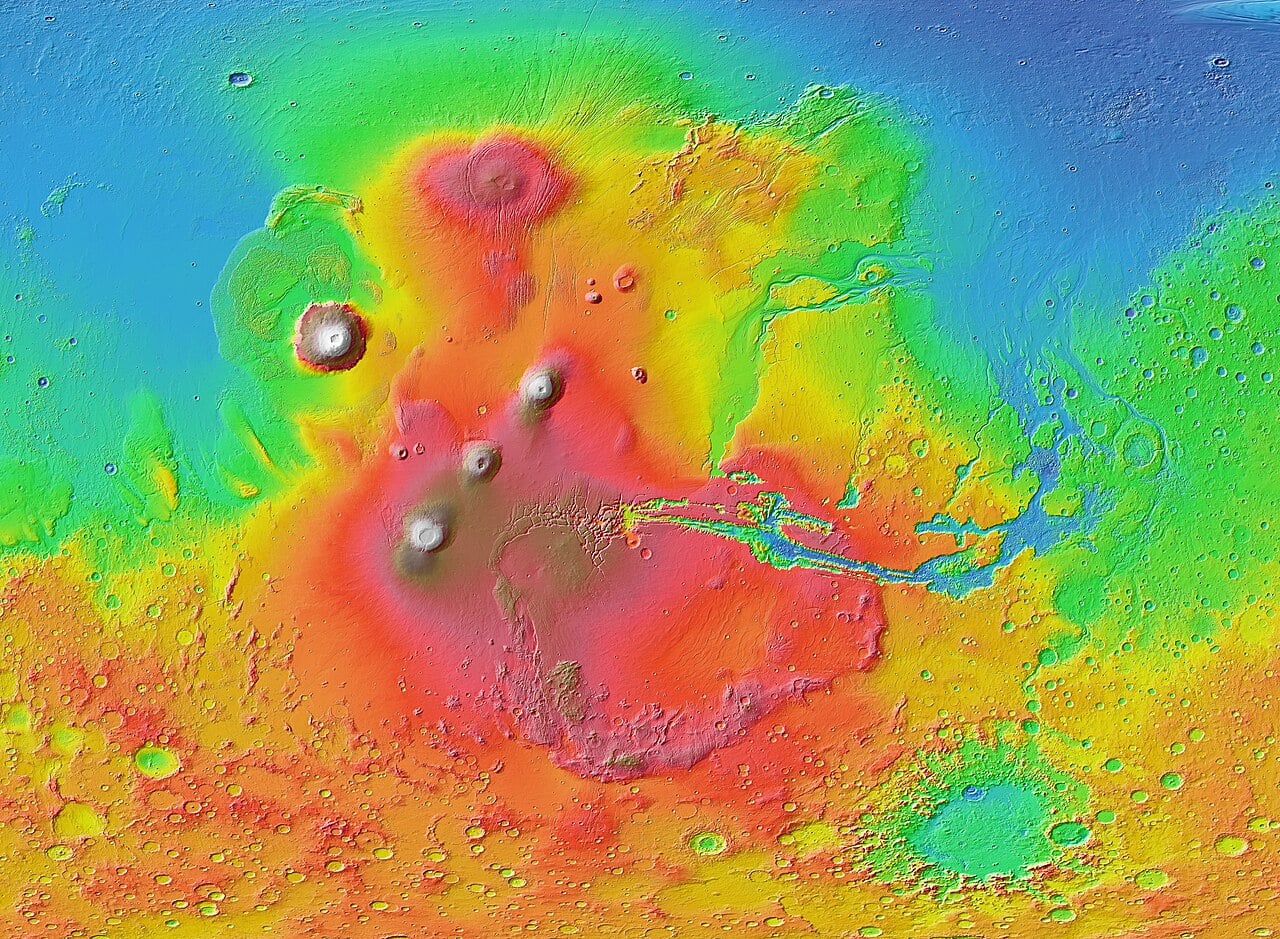 WWW.UNIVERSETODAY.COMThe Hidden Story of Young Martian VolcanoesNew research has revealed that Mars most recent volcanoes werent formed by simple, one off eruptions as scientists previously thought. Instead, these volcanic systems evolved over millions of years, fed by complex underground magma chambers that changed and developed over time. By studying surface features and mineral signatures from orbit, researchers have pieced together a far more intricate volcanic story than anyone expected.0 Comments 0 Shares 0 Views
WWW.UNIVERSETODAY.COMThe Hidden Story of Young Martian VolcanoesNew research has revealed that Mars most recent volcanoes werent formed by simple, one off eruptions as scientists previously thought. Instead, these volcanic systems evolved over millions of years, fed by complex underground magma chambers that changed and developed over time. By studying surface features and mineral signatures from orbit, researchers have pieced together a far more intricate volcanic story than anyone expected.0 Comments 0 Shares 0 Views -
 WWW.GAMEBLOG.FRThe Division : de grandes annonces sont en approche pour la franchise, c'est officielAlors que The Division sapprte officiellement clbrer son dixime anniversaire, Ubisoft nous promet de grandes annonces et de belles surprises venir ds le mois prochain.0 Comments 0 Shares 0 Views
WWW.GAMEBLOG.FRThe Division : de grandes annonces sont en approche pour la franchise, c'est officielAlors que The Division sapprte officiellement clbrer son dixime anniversaire, Ubisoft nous promet de grandes annonces et de belles surprises venir ds le mois prochain.0 Comments 0 Shares 0 Views -
 WWW.GAMEBLOG.FRTomb Raider : un nouveau collector ultra rare annonc, les fans vont adorerVous tes fans de Tomb Raider et collectionneur ? Alors vous ne voudrez sans doute pas passer ct de cette nouvelle figurine ultra collector signe Dark Horse.0 Comments 0 Shares 0 Views
WWW.GAMEBLOG.FRTomb Raider : un nouveau collector ultra rare annonc, les fans vont adorerVous tes fans de Tomb Raider et collectionneur ? Alors vous ne voudrez sans doute pas passer ct de cette nouvelle figurine ultra collector signe Dark Horse.0 Comments 0 Shares 0 Views -
 YUBNUB.NEWSTrump to Outline Multi-Billion-Dollar Gaza Rebuild and International Stabilization Force at Board of Peace SummitPresident to chair first formal Board of Peace meeting as global delegations gather in Washington to discuss reconstruction fund and security deployment for Gaza. By yourNEWS Media Newsroom President0 Comments 0 Shares 0 Views
YUBNUB.NEWSTrump to Outline Multi-Billion-Dollar Gaza Rebuild and International Stabilization Force at Board of Peace SummitPresident to chair first formal Board of Peace meeting as global delegations gather in Washington to discuss reconstruction fund and security deployment for Gaza. By yourNEWS Media Newsroom President0 Comments 0 Shares 0 Views -
Why Choosing Wine Before Your Meal Can BackfireWhy Choosing Wine Before Your Meal Can Backfire...0 Comments 0 Shares 1 Views
-
 WWW.LIVESCIENCE.COMHow long do most planets last?Planets are born, and they can also "die." So what's the lifespan of a typical planet?0 Comments 0 Shares 0 Views
WWW.LIVESCIENCE.COMHow long do most planets last?Planets are born, and they can also "die." So what's the lifespan of a typical planet?0 Comments 0 Shares 0 Views -
Worried about your digital privacy? I tested the top 3 VPNs to find the best of the best.The 3 best VPNs of 2026 will make you feel like a ghost Here's who to trust with your privacy (and money). By ...0 Comments 0 Shares 0 Views
-
AdGuard is your one-time fix for pop-ups, autoplay ads, and online tracking — now $16AdGuard is your one-time fix for pop-ups, autoplay ads, and online tracking — now $16 TL;DR: Through Feb. 22, grab a lifetime AdGuard Family Plan for $15.97 (reg. $169.99) and remove ads and trackers on up to nine devices for good. $15.97...0 Comments 0 Shares 0 Views
-
Economic strike effort: Quit these tech services'Resist and Unsubscribe' strike targets tech companies The way marketing professor Scott Galloway puts it, the primary way to get President Donald J. Trump's attention is by influencing the market. Don't like Trump's deployment of immigration authorities to Minneapolis or the killings of Americans observing the agents' actions? Find a...0 Comments 0 Shares 0 Views


